NU 2025-001
INVENTORS
- Venkatramanan Subrahmanian* (McCormick School of Engineering, Computer Science)
- Andrew Pulver
- Andrea Pugliese
- Jiazhi Zhang
- Saurabh Kumar
- Valerio La Gatta
- Youzhi Zhang
SHORT DESCRIPTION
This technology automates covert influence campaigns on social media. It leverages reinforcement learning to balance user impact with minimal detection risk.
BACKGROUND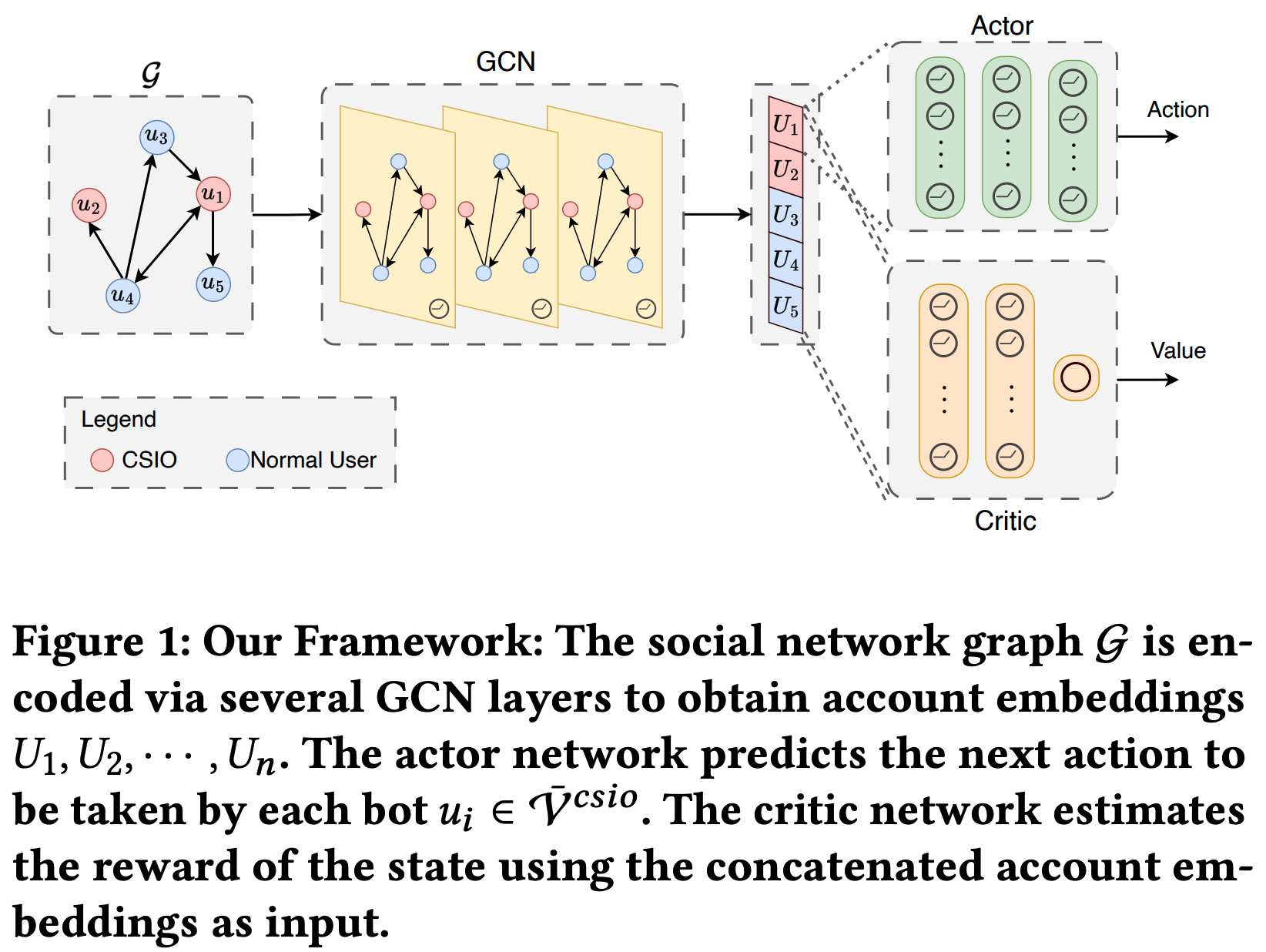
Social media platforms face evolving detection algorithms that often flag aggressive influence operations. Current methods struggle with precise control over campaign influence and stealth. There is a clear need for tools that can simulate covert information operations while managing detection risks.
ABSTRACT
The invention uses reinforcement learning to autonomously run covert social influence operations. It combines actor-critic principles with the Proximal Policy Optimization algorithm. In IRB-approved trials lasting five days, the system executed four campaigns using a 225-subject panel. Results confirm that the system effectively balances influence maximization with low discoverability, showcasing nuanced operational trade-offs.
MARKET OPPORTUNITY
The global market for social media security is projected to grow from $1.89 billion in 2022 to $7.21 billion by 2029, at a compound annual growth rate (CAGR) of 21.1%. This expansion is driven by the increasing use of social platforms for sophisticated information warfare by state actors, as well as by non-state groups for complex disinformation and fraud campaigns. The primary market for this technology includes government defense and intelligence agencies, cybersecurity firms, and threat intelligence organizations that conduct adversarial simulation or "red teaming" exercises. (Source: MarketsandMarkets: "Threat Intelligence Market - Global Forecast to 2028").
DEVELOPMENT STAGE
TRL-4 - Prototype Validated in Lab: Key functions have been demonstrated in IRB-approved lab trials simulating covert social media campaigns.
APPLICATIONS
- Covert influence campaign simulation: Supports cybersecurity research efforts.
- Training tool for misinformation detection: Enhances digital defense strategies.
- Social media strategy optimization: Allows controlled testing of influence techniques.
- Academic research platform: Facilitates studies on online information dynamics.
ADVANTAGES
- Balances influence and stealth: Minimizes risk of detection while maximizing impact.
- Enables autonomous operation: Runs campaigns with minimal human oversight.
- Empirically validated: Demonstrated success in controlled, IRB-approved trials.
- Adapts to dynamic environments: Adjusts strategies in real time to changing conditions.
PUBLICATIONS
IP STATUS
U.S. Patent Pending